G DATA analysts have discovered a new security threat in Word documents. Users are promised corrections of invoices or other bonuses. In order to claim those, they are supposed to open an attached Word document. This document contains malicious code that leads to the installation of the well-known Emotet malware and prepares a computer for the installation of further malware.
The mails in question are sent under a false name, often posing as messages from friends or business partners of the potential victims. However, the mail addresses are only superficially forged, a glance at the detailed e-mail header shows the original sender addresses. A concrete example in the G DATA SecurityLabs has the subject line "payment letter".
Hardly any legitimate use for macros
In order for the malware to be installed, however, users must agree to the execution of macros. However, this option should never be selected for documents from the Internet, as there are hardly any use cases for the macros, especially for private users. In the current campaign, however, users are to be persuaded with a particularly perfidious trick to allow active content.
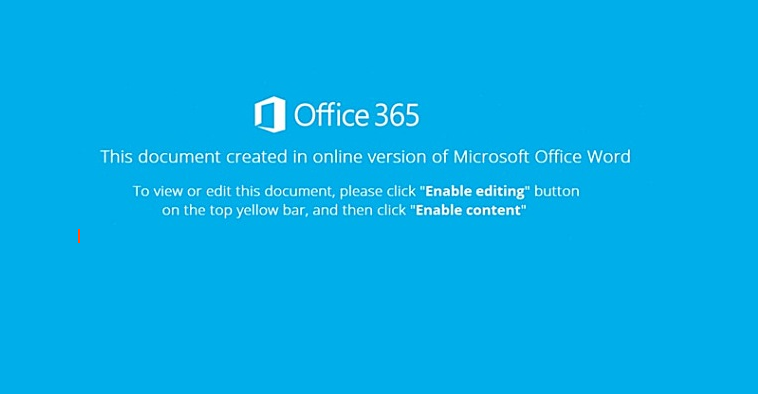
The document is coloured blue and it shows a reference that the file was created using a Web version of Office. Therefore, users would have to unlock the active content. If they do this, the macro in the background opens the Windows Powershell and loads further malware. Emotet is used here. We have already reported about this malware several times in the G DATA Security Blog. Emotet can permanently implant itself on a system and then opens a back door for the installation of further malware.
On the computer, an exe file is created in the folder for temporary files, which has three random numbers as names. In addition, the system tries to access randomly generated URLs of the domains colexpresscargo.com, notehashtom.ir, corporaciondelsur.com.pe and farmasi.uin-malang.ac.id. Probably these are insufficiently secured, actually legitimate websites, which were taken over by the criminals.
G DATA security tips
G DATA security solutions already recognize numerous variants of the malware, for example under the name VB.EmoDldr.12.Gen. Criminals, however, further develop the malware in a very short time, so that new versions are circulating again and again. In addition to installing an antivirus solution, users should therefore always observe the following rules when handling e-mails:
1) Unwanted e-mails sent by third parties should always be viewed critically, especially if they contain attachments.
2) For private users there are hardly any applications for macros and other "active elements". They should therefore not be activated at all. Also in the enterprise context there are only limited purposes for macros, these are usually used only in special forms.
3) In case of doubt: Just ask if the mail actually comes from the sender. If the sender is known, it is best to make a quick personal call or ask via a messenger.
Information for fellow analysts:
SHA256: 18bf984f55b165527e4fa212bb339890259e44f6356bd8df712ba324c19874d0
MD5: e7dc239954041896e6ae74abd03ce15c
