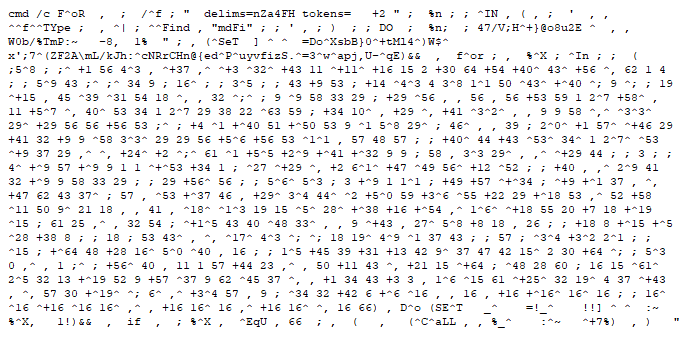
G DATA security experts have successfully identified and investigated the first in-the-wild occurrence of a malware downloader obfuscated using a method that had not been used previously. Batch and power shell commands are hidden in such a way that they are not immediately recognizable even by experienced analysts. Malware authors use obfuscation techniques to defer analysts from reverse-engineering their code.
"We have never seen malware in the wild before that uses this kind of obfuscation", says G DATA malware analyst Sascha Curylo, who was finally able to crack the code. "When we first looked at the sample, our initial thought was that we had extracted the file incorrectly. "It was only after detailed analysis that we were able to identify the hidden commands."
In fact, the extracted code initially looks like a random collection of characters. However, many of the spaces, commas and some other characters are not interpreted at all by the Windows command line and can therefore be removed without changing the result, says Curylo. After this treatment, the term can then be better interpreted by analysts. For example, certain recurring patterns in the long strings indicated that the result is a URL that is contacted for further instructions.
Commands are hidden by "Dosfuscation“
After a thorough analysis, it turns out that the malware downloader uses a new method to hide the actual malware. It was first described under the name Dosfuscation by security researcher Daniel Bohannon. Substrings and numbers are used to assemble command sequences from individual letters. So far, however, no malware sample was known to use this method for active attacks.
The sample analyzed by G DATA was sent in under the name Rechnung-Details-DBH[random number sequence].doc by a customer. Virus Total has many other document names with the same malware, most of which try to mimic invoice names ("Rechnung" is also the German word for "Invoice"). Our sample Word file executes a macro that contains more obfuscated code.
What is Obfuscation?
Obfuscation refers to various techniques used to modify the source code of a program in such a way that it is difficult for analysts to analyze. The effort for reverse-engineering of malware thus increases significantly. In addition, the malware cannot be easily detected by automated analyses. To obfuscate code, for example, individual letters can be replaced by others, and individual components of a program or files can also be encrypted.
This macro then starts the obfuscated batch code with which the command line is opened and controlled. At this point in time a powershell downloader is started and another downloader named Emotet is downloaded. The malware was initially used as a banking Trojan, but over time has developed into a modular downloader and infostealer.
The actual payload used in the current attack is another malware called Trickbot, which is mainly known for attacks on online banking. Trickbot is downloaded by the Emotet malware.
Information for fellow researchers:
SHA256: 880dbab81729e3cd7cd1bd64023de55f2a6ac4e0d08ebbf2b30722d06933c8a8
MD5: 41ce357e792fdbc426609aa1dbc8416a