What is Fortnite?
Fortnite (proper name Fortnite Battle Royale) is a video game that is currently available for PC, Mac, consoles and iOS. According to developer information, the game currently has 125 million registered users and addresses a relatively young target group - the retail version bears the USK (Entertainment Software Self-Regulation Body) “12 and above” seal. The publication of the iOS version shows how successful it is. In the first three weeks alone, Fortnite recorded revenues of over 15 million dollars. That is a higher revenue than Pokemon Go, for example. Currently, the developer earns around $1 million a day with Fortnite only on iPhone and iPad.
Fortnite's popular Battle Royale mode is quickly explained: A total of 100 players compete on a small card in this third-person shooter. The goal is simple: the last person standing has won.
The developers of the game have announced an Android version of Fortnite for the summer of 2018. As Fortnite has already been available for iOS for some time, the impatience among Android users is also naturally increasing.However, the problem for the developers is the diversity of Android. There are numerous devices that use different versions of the operating system. A complex app must therefore function simultaneously on every Android device, or otherwise incur the wrath of gamers. G DATA has denounced this dilemma numerous times in the past, as it also poses a risk for IT security. Criminals will exploit this curiosity and impatience when Fortnite for Android finally appears.
Subscription and malware traps
Dozens of videos on portals such as YouTube offer supposed instructions for installing Fortnite on Android devices. New clips are added every hour. These fraudulent videos are designed to adress younger gamers. In the end, they install non-functional apps on their devices, which only cause damage and frustration instead of fun. We have identified four popular scams here:
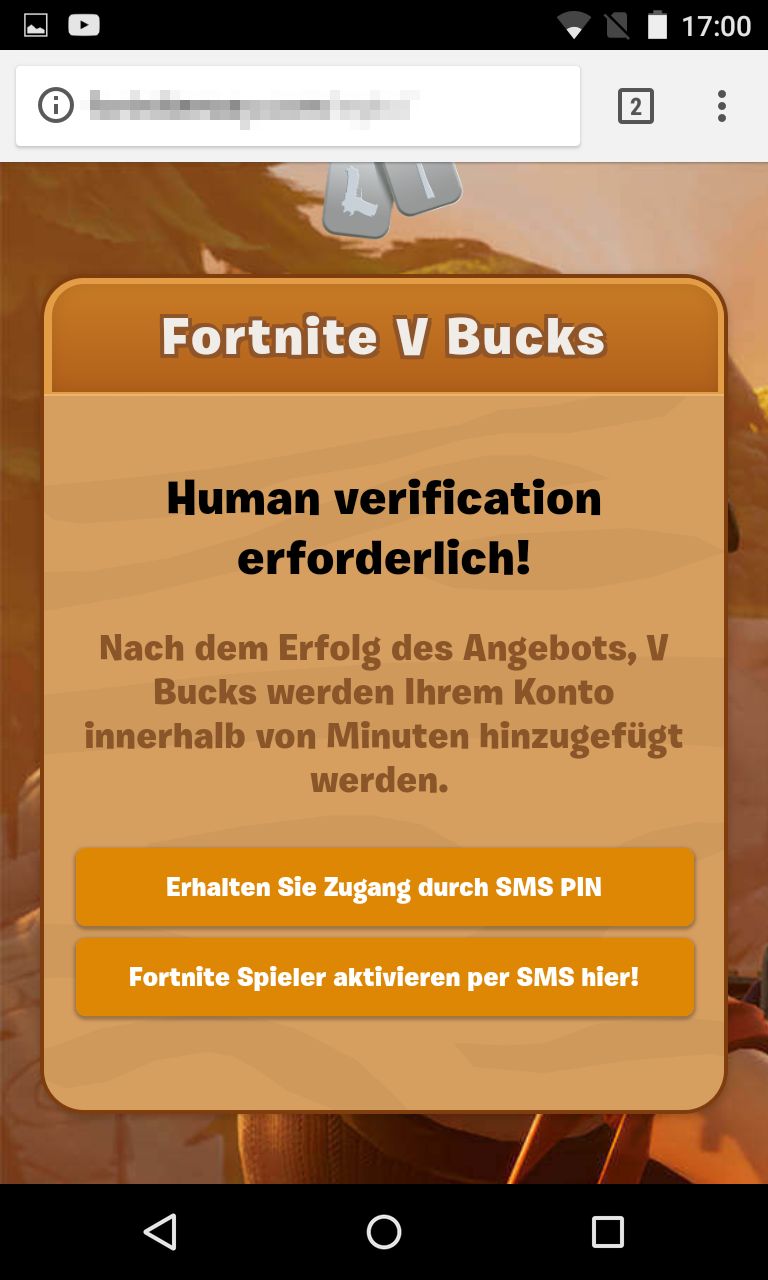
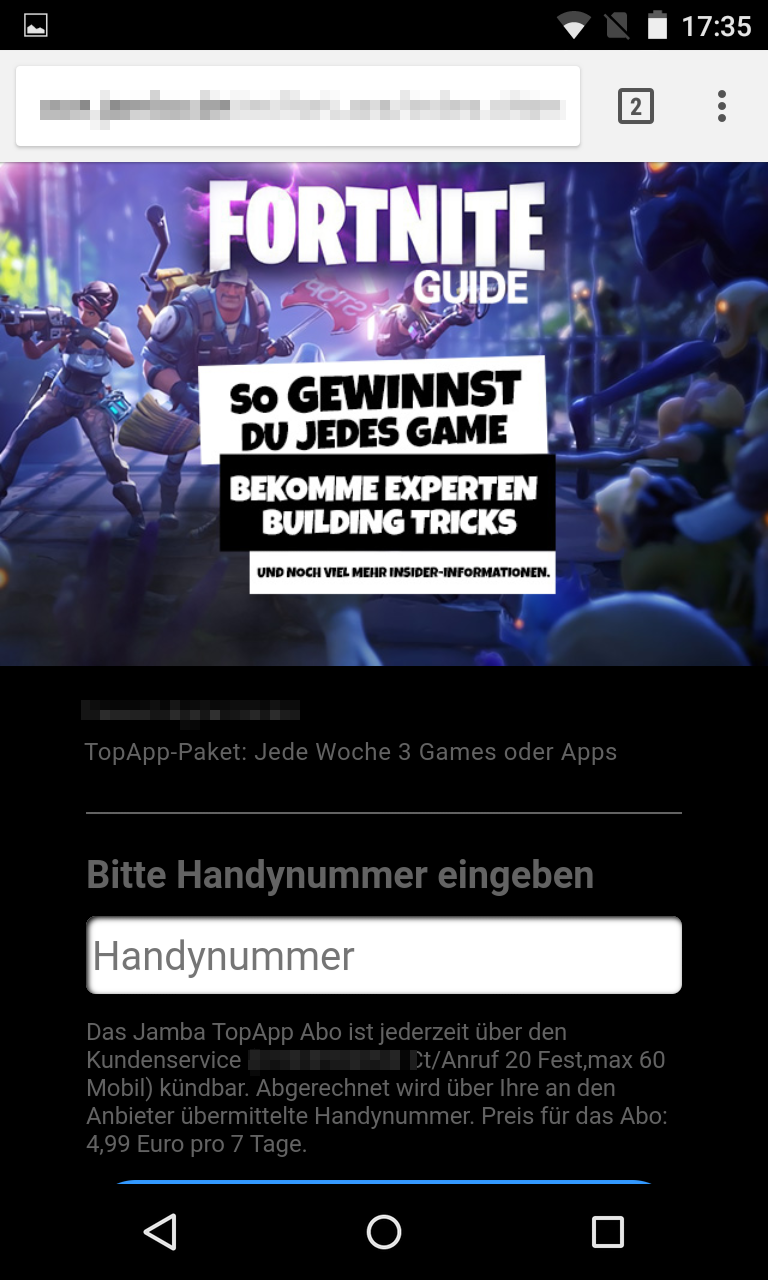
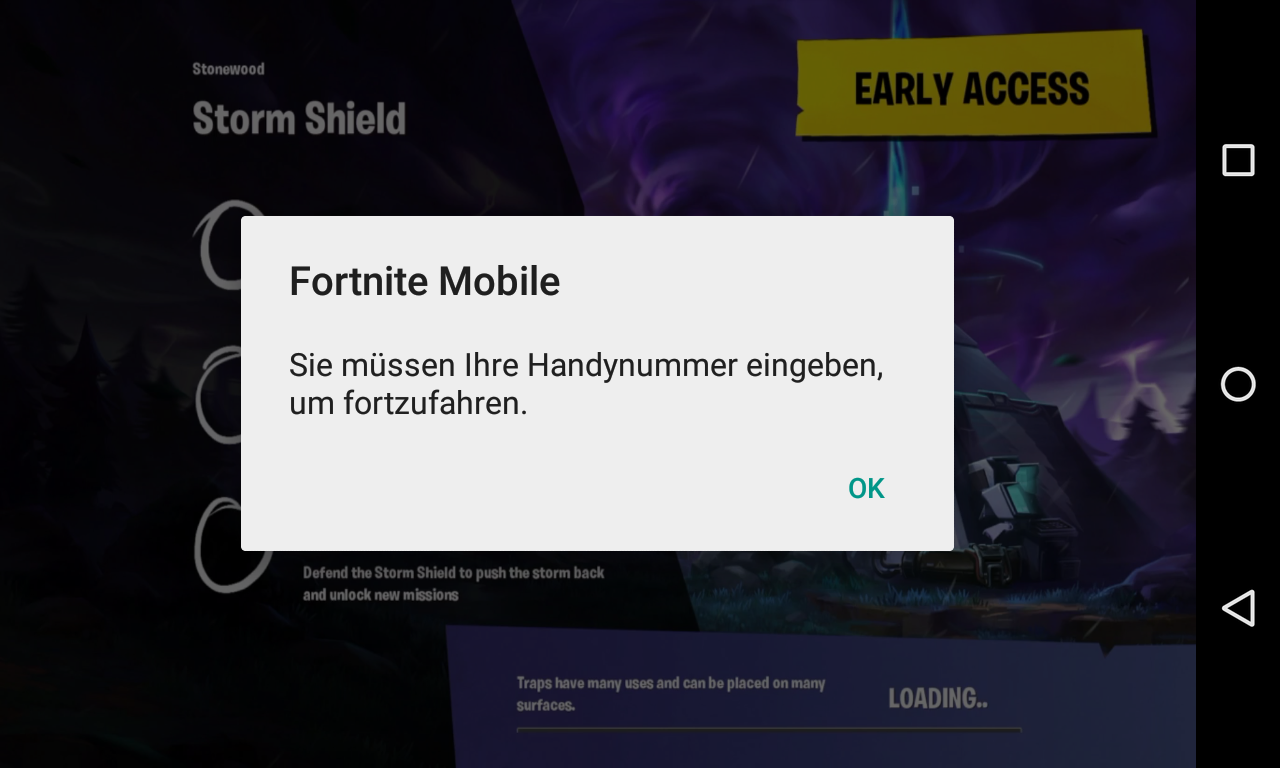
Scam 1: Fake sites pretend to belong to the developers and offer supposed Fortnite apps. Users are asked to enter their mobile number on these websites. In the small print it says that the users are agreeing to an SMS subscription for three to seven Euros a week. In one example, no fewer than three subscriptions were agreed at the same time.
Scam 2: Equally risky is the scam where malware gets into the system via a manipulated app. This Remote Access Trojan (RAT) gives the cyber criminals full access to the device. In this way, sensitive data can be stolen or more malware subsequently installed.
Scam 3: Another fraudulent scam is fake apps that target access data.
Scam 4: Other developers try to use an alternative of the app with a similar sounding name to profit from the enthusiasm for Fortnite.
G DATA security solutions protect customers from this malware and block such phishing sites.
G DATA tips:
- Only download apps from official sources: Google checks applications uploaded to its own store for malware. Suspicious or malicious applications are usually rapidly removed from the Play store. However, on platforms that are not checked by Google or the smartphone manufacturers and where there is no filtering, the risk of picking up a malicious app is generally significantly higher.
- Set up third-party vendor blocks: A “third-party vendor block” can be set up with the mobile network provider. This makes it impossible for expensive subscriptions to be agreed. Providers have various names for this, such as “Added value services”. The provider is legally required to set up such a block at the request of the mobile network user.
- Install a security solution: Users should also install a security solution on their Android smartphone, such as G DATA Mobile Internet Security. This has recently been selected again as a winner by AV-Test.
- Parents should support their children: Parents should be open to their children's experiences and interests on the net. Mothers and fathers should be shown the applications and talk about their children's experiences with the online media. Parents should be aware of the possible dangers on the Internet so that they can also make their children aware of them.
Informationen for fellow researchers
SHA256:
11dee9f3f633cb22d3a50a1c55ae6bbfb437b6af8b4446c6feb2021ebd799163
390094c34e1d0384f65850ac3d72545176df6e93eb470f20fd2bf603a4c94093
5047e9fcd6393927c27e560a2b98e604a3c40af44ff31cbd32138d9e9346efef
ef458409e7e818903965b6353b557ffdd2d85d68e0b1313a24e5fc36c47f8332
c9d07ad4dbd0beaf9d0b5bafc69a07b7f7135d245d1ef98ca221cef0cbcfa064