On average, everybody has 19 passwords he needs to remember, some of which are used on a daily basis, some used less frequently. This is the author’s list, just as an example:
- ATM & credit card: two PINs
- Email accounts: various
- Social networks: four
- Discussion boards: three
- Password for work PC
- Password for home PC
- Passwords/PINs for smartphone / tablet: three
- Dropbox
- iTunes
- Online banking
- PayPal
- …
The list goes on. In addition, you are also forced to change some of your passwords every once in a while. One example for this would be the PC at work; the policy of the IT department dictates a password change every few weeks. When a service or account is not used for an extended period of time, you might forget the password altogether – and when you create a new one, you may find yourself facing an error message which tells you that the new password is not secure enough: it is either too short, not complex enough, doesn’t contain enough special characters or is too similar to the old password.
Path of least resistance
For this reason, people try to make things easier for themselves: the same password is then used in four or five different services and only needs to remember one. What looks smart and efficient is in fact the opposite. This practice greatly compromises security. Security experts have good reason to warn of this password reuse: should the password be stolen which is used for email and social media accounts, an attacker has direct access to your complete online identity. This is very similar to losing a master key which unlocks most, if not all doors in a building.
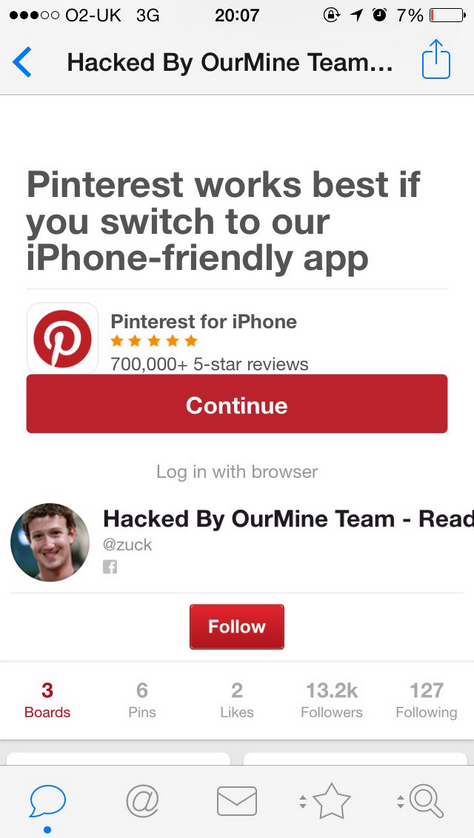
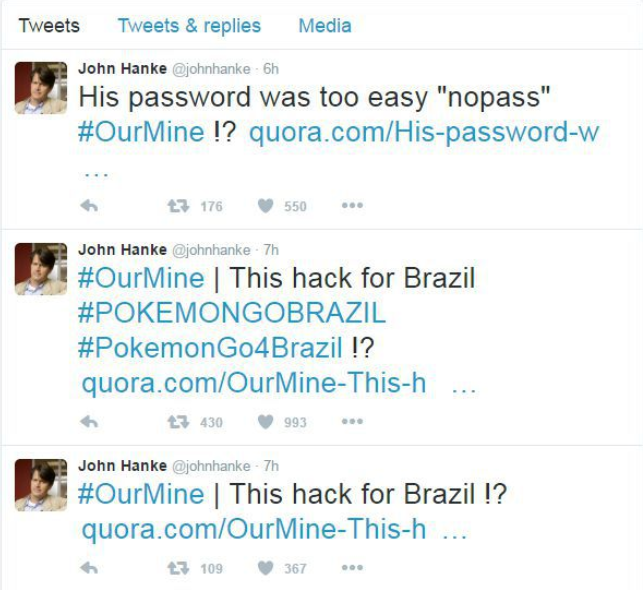
Current news coverage clearly shows that weak passwords are a problem across all areas. In the wake of the LinkedIn data breach, all passwords were evaluated and it turned out that the password "123456" was used more than 763.000 times. In second place, far behind this, comes the password ‘linkedin’, with 170.000 instances. Even people like Mark Zuckerberg were not spared: his prominent examples demonstrates the trouble that password reuse can get a user into. In his particular case he appeared to have used the same password for LinkedIn, Pinterest and Twitter. His password of choice was ‘dadada’. Granted, this password does not show up in the list of the 50 most frequently used passwords, but it remains a poor choice for a password. It did not take long until a group that calls itself ‘OurMine Team’ used the access credentials to log into Zuckerberg’s Pinterest account to make the successful ‘hack’ public. The same group also claimed responsibility for hacking the Twitter account of John Hanke. If you are not familiar with his name you might know his company Niantic; they have released mobile games such as Ingress – and Pokémon Go, which we reported already about.
Another fact that is often overlooked is that in most cases, passwords are not ‘cracked’ - they are in fact stolen. Trying to ‘crack’ a password by trying out different passwords mostly is too time-consuming and requires too much work. Certain frequently used passwords might be tried out by specific types of malware such as Morto as well as a few types of ransomware but it takes far less effort to try and steal passwords at the source.
Secure passwords, however, are not the be-all and end-all of security. Providers of online services must make sure that passwords cannot be stolen by an attacker. If a service is improperly secured, a strong password is of little use. This is what happened in the case of the infamous LinkedIn data leak. The user database was secured in a way that was not up to par with current standards: user data was secured using a deprecated hashing algorithm. LinkedIn had also failed to use additional cryptographic measures (salting) to secure access to the data.
Alternatives and how to leverage
Several approaches exist which promise help or an alternative when it comes to passwords. Each of them has it advantages and its drawbacks.
Password Managers
The principle is very simple: you generate a password that is complex and long enough to fulfill any password requirement, but you don’t have to remember it – the program does that for you.
Solutions are plentiful, whether it is a locally installed or a cloud-based solution, whether it is open source software or proprietary. You only have to remember one single complex password which you do not use anywhere else – the program does the rest for you.
Hardware Tokens
Whether it is a Smartcard, RFID token, a smartphone or some other piece of hardware, the principle is to tie the process of accessing a virtual resource to a physical item which cannot be forgotten or compromised, unless it is physically acquired by someone else. What keeps many users as well as providers from using and offering this alternative is the fact that additional hardware must be purchased. In addition to this, a hardware token is relatively cumbersome to use compared with just entering a password or scanning a fingerprint. Combining hardware tokens with One Time Passwords (OTP) which are only valid for one login process will improve security even further. The security of token-based authentication can also be achieved through a smartphone, for example by installing an app which creates an OTP.
Biometrics
Instant access at the touch or swipe of a button is what providers of biometric authentication promise. Biometrics rely on the uniqueness of certain features in our bodies, such as fingerprints, iris patterns, the layout of blood vessels in a hand, the way we type or the sound of our voices. The user himself becomes the access token, which also makes it impossible to lose a token (unless the token is forcibly removed which might destroy it) and makes the requirement to buy a new one obsolete. Some limitations apply: A system might fail to recognize a voice in case the user has a bad cold and a stuffy nose. Also, you cannot really keep biometric features secret; if someone records you speaking your pass phrase then this might be a problem. The same applies to fingerprints. Those can become unreadable in dusty or wet environments and in case of injury. Iris/retina scanners in some cases are uncomfortable to use when they shine a very bright light into your eyes. They also might not work for authentication purposes if certain medical substances are used - or in case of injury.
Careful calibration is required to minimize the false-accept and false-reject rate.
(a little random science fact on the side: identical twins do in fact have different fingerprints). Unless you are referring to fingerprinting, the financial threshold for biometrics is rather high: a palm vein or retina scanner will set you back several hundred dollars.
Where to start?

Looking at all the considerations of security vs. comfort vs. cost of implementation it seems that passwords are here to stay, but in order to protect our identities, privacy and money, measures must be taken to enhance their security.
Users are best advised to use a password manager as their baseline – some password managers can also create strong and complex passwords automatically. This should not be underestimated, either - making passwords ever longer makes them impractical to use and near impossible to remember. On top of this, a human-generated password often is too easy to guess.
There are things that can be done about this. A password manager saves this information and accesses it as soon as it is needed.
It is also worthwhile to be on the lookout for reports about data breaches. As soon as a data breach of a platform during which password were potentially exposed, the password should be changed as soon as possible. The measures can and should be extended to other services as well in case your email provider falls victim to a data leak. Should an attacker get access to your main email address he can then exploit the fact that many providers of online services allow their users to reset their password. All that is needed is the email address. Therefore, if your email account is compromised, a criminal in theory has full access to your online identity and can steal it by changing all passwords.
A combination of different authentication method can further improve security. This concept is also referred to as ‘two factor authentication‘ (2FA). This combines ‘something you have’, like a hardware token or smartphone, with ‘something you know’, in other words a password. Alternatively, you could combine ‘something you know’ with ‘something you are‘ – this is where biometrics would fit in. A fingerprint is always unique and inseparable from a person. That way a system can be reasonably sure that the person who enters the password is identical to the person who puts the finger on the fingerprint reader.
Security can be improved significantly with this method as opposed to only relying on a password. An attacker will always need two things in order to take over an online account which is secured in that manner. Some platforms are offering this type of account security as an option to their users.
Four tips to improve your online accounts’ security
- Check the websites www.leakedsource.com or www.haveibeenpwned.com and search for your email address or username. If a result shows up: don’t panic. A result does not mean that your account has been abused. Change the password immediately or delete the account in case you are not using it anymore.
- Install a password manager
The principle is very simple and straightforward: you generate a password which is complex and strong enough to meet all complexity guidelines but you do not need to remember it – the program does this for you. In its latest version of TotalProtection, G DATA offers a password manager. After installing, it will appear in your browser as an icon and it stores all access data of websites which are used to access password-protected accounts. - Review your passwords and change them if needed
To get an overview it might help to write them down on a piece of paper. As soon as you discover that you have used the same password for multiple accounts, change it. Changing the password does not mean “add an iterating number to it”, like password1, password2 etc. Come up with a new password or have your password manager generate one for you. - Use two-factor authentication where possible
The option might be called differently, for example “Two-step verification” or “Login approvals” or something along those lines. Facebook, LinkedIn, Dropbox, Google, PayPal and a few other networks offer this as an option.