G DATA’s SecurityLabs experts are constantly analyzing the threat landscape computer users are facing. Our Malware Report for the second half-year 2015 has now been published. Check out the most important findings:

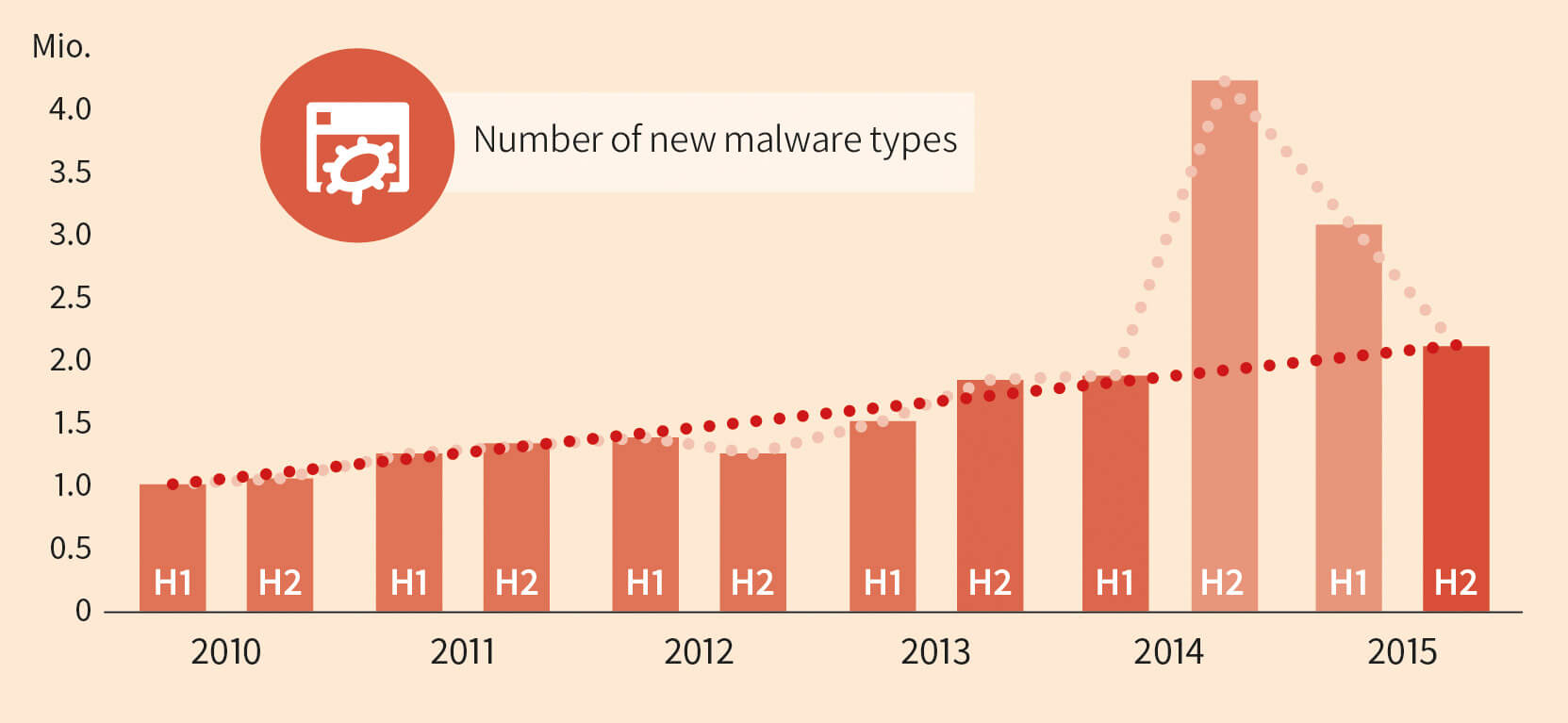
- In the second half of 2015, experts at G DATA SecurityLabs recorded 2,098,062 new signature variants. This number is 31% less than in H1 2015.
- At 5,143,784, the total number of new signature variants in 2015 was only slightly less than the figure for 2014.
Threat Monitor and dangerous websites
- A look at the reported attacks shows that the Risk Monitor Top 10 covers 39.6% of all those reported. PUPs and adware continue to be dominant here.
- Script.Adware.Dealply.G takes 1st place in the ranking, with 22.9% of all attacks assessed. This browser add-on, which is frequently installed without being noticed, transmits and uses user data that can then be used for various purposes by the developer company.
- In the categorisation of evil websites, the Gambling category is particularly prominent. In the last six months, it has jumped from 13th place to 1st place (18.7%) in the rankings.
- When looking at the countries in which the servers with evil websites are located, the USA was again out in front in this half-year. Around 57% of recorded attacks originated from here. Germany is in 3rd place, with 3.9%.
- The banking Trojan Swatbanker, which was responsible for the highest number of averted attacks since records began (March 2015), almost completely disappeared from the picture.
- Another massive attack by Dridex was recorded at the end of the year. The banking Trojan has been seen before, and it can be assumed that it will continue to be active.
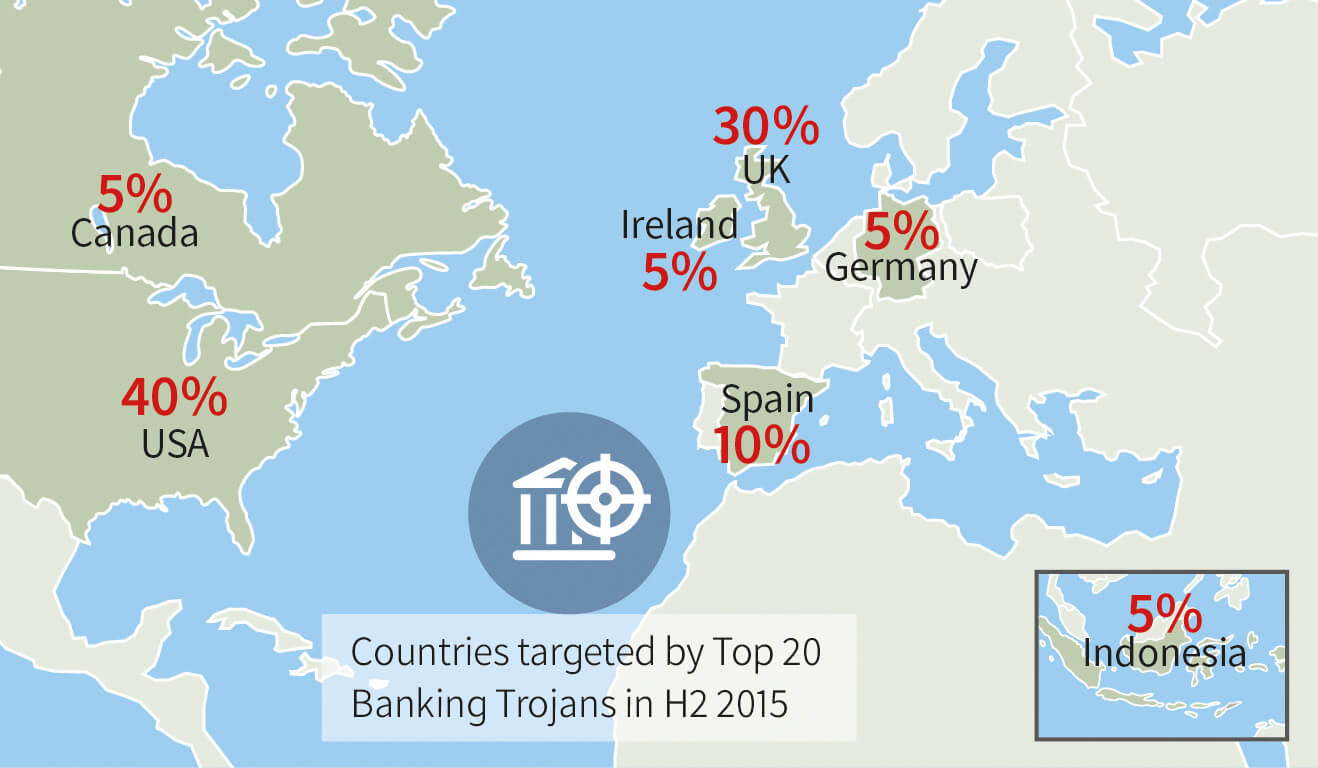
- The assessment of targets of banking Trojans confirms the observation that the Anglophone region continues to be the main target of the attackers. 80% of all target sites identified came from English-speaking countries.
- The Neutrino, Angler, Nuclear and Magnitude exploit kits were particularly prominent in the second half of 2015.
- The attacks on Hacking Team led to information on previously unknown vulnerabilities ending up in the hands of cyber criminals, being built into exploit kits and causing one of a number of waves of attack.
- It was conspicuous in this half-year that two major waves of attack (evidently in the Hacking Team case, presumably in the case of APT28) can be traced back to attack tools used at the government level that have been adapted by cyber criminals.
Download G DATA's half year report now: